JHDD Ransomware joins the STOP/Djvu Ransomware Family
JHDD Ransomware is another addition to the STOP/Djvu Ransomware family. Like its predecessors, it locks files and demands a ransom fee to restore file access. If you often install applications from unreliable or questionable sites, you could eventually expose yourself to threats like JHDD Ransomware.
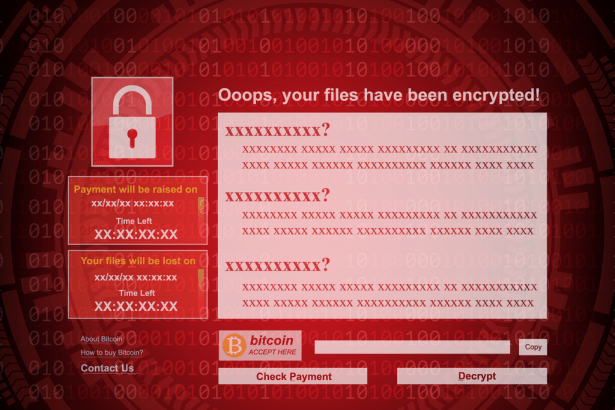
JHDD Ransomware corrupts various file types, including photos, music, documents, and videos. During the file encryption, JHDD Ransomware adds the .JHDD extension to affected files and leaves a ransom note on the user’s desktop and in every folder that has the encrypted files.
Unfortunately, a free decryption tool for JHDD Ransomware is not available at the moment. The few reliable ways to recover affected files is to restore them from a data backup or look for an online data recovery service that can investigate your ransomware incident.
There is no guarantee that the cybercriminals behind JHDD Ransomware will issue the decryption key they promise, so ransomware victims are discouraged from paying the ransom.
JHDD Ransomware employs distribution methods that are common among many other ransomware variants. It generally arrives via malicious spam emails or unreliable websites. Once the malware accesses the victim’s system, it employs the AES encryption algorithm to lock up important files. Afterward, JHDD Ransomware demands a ransom in exchange for the decryption key. The decryption key costs $980, but the cybercriminals will offer a 50% discount if the victim contacts them within the first 72 hours after infection.
How Do I Deal with the JHDD Ransomware Infection?
To protect yourself from the JHDD Ransomware infection, you should invest in a reputable malware remediation tool to regularly scan for elements associated with this troublesome ransomware infection. What’s more, you should also back up your files on an external hard drive or cloud storage.