Clone ransomware, a member of the notorious Dharma ransomware family, has been wreaking havoc on computers worldwide. It primarily targets user files, encrypting them and demanding a ransom for their decryption. This article will provide a detailed analysis of Clone ransomware, including its threat type, encryption methods, ransom note details, and distribution methods. We will also explore how to remove this malware using SpyHunter and offer preventative measures to avoid future infections.
Clone Ransomware Overview
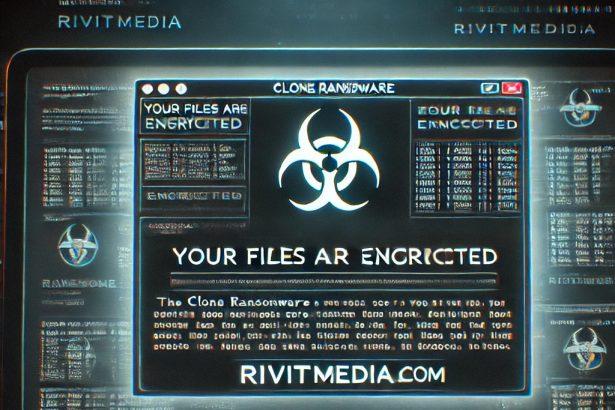
Clone ransomware is a type of crypto virus or file locker that encrypts files on the infected system and appends a .Clone extension to them. After encryption, the attackers demand a ransom in exchange for decryption keys. This ransomware is part of the Dharma family, which is infamous for its persistence and destructive capabilities.
Once it infects a system, Clone encrypts files stored on both local and network-shared drives. The ransomware ensures that system files are not targeted, meaning that the infected device remains operable. However, the encrypted files become inaccessible without the decryption key.
Threat Summary Table
| Attribute | Details |
|---|---|
| Threat Type | Ransomware, Crypto Virus, File Locker |
| Encrypted Files Extension | .Clone (files also appended with a unique ID and cyber criminals’ email address) |
| Ransom Note File Name | clone_info.txt |
| Cyber Criminal Email Addresses | CloneDrive@mailum.com, CloneDrive@tuta.io |
| Detection Names | Combo Cleaner (Trojan.Ransom.Crysis.E), DrWeb (Trojan.Encoder.3953), ESET-NOD32 (Win32/Filecoder.Crysis.P), Kaspersky (Trojan-Ransom.Win32.Crusis.to), Microsoft (Ransom:Win32/Wadhrama!pz) |
| Symptoms of Infection | Files cannot be opened, file extensions changed to .Clone, ransom demand displayed on screen |
| Damage | Files encrypted and inaccessible, potential installation of additional malware, and data theft |
| Distribution Methods | Infected email attachments (e.g., macros), malicious ads, torrent websites, drive-by downloads, malicious links or attachments in spam emails |
| Danger Level | High — Data loss, financial loss due to ransom demands, potential installation of additional malware |
Download SpyHunter Now & Scan Your Computer For Free!
Remove this and any other malicious threats to your system by scanning your computer with SpyHunter now! It’s FREE!
Ransom Note Details
Upon infection, Clone ransomware drops a ransom note both in a pop-up window and as a text file named clone_info.txt. This note demands that the victim contact the cyber criminals via email to pay the ransom. The attackers suggest that the decryption process is possible but caution against seeking help from third parties, likely to prevent the use of alternative decryption methods.
Here is a summary of the text presented in the pop-up and ransom note:
Pop-up Message:
CLONE
YOUR FILES ARE ENCRYPTED
Don't worry, you can return all your files!
If you want to restore them, write to the mail: CloneDrive@mailum.com YOUR ID -
If you have not answered by mail within 24 hours, write to us by another mail: CloneDrive@tuta.io
ATTENTION
CloneDrive does not recommend contacting agent to help decode the dataRansom Note Text File (clone_info.txt):
You want to return?
write email CloneDrive@mailum.com or CloneDrive@tuta.ioThe email addresses provided by the attackers, CloneDrive@mailum.com and CloneDrive@tuta.io, are used for communication during the ransom negotiation process.
How Clone Ransomware Infects Your System
Clone ransomware typically spreads through various infection vectors, including:
- Phishing emails: The malware is often bundled with malicious email attachments or links.
- Malicious ads: Ads displayed on compromised websites can serve as delivery mechanisms for Clone.
- Torrent websites: Fake or malicious files uploaded to torrent sites can contain ransomware payloads.
- Drive-by downloads: Visiting compromised websites can trigger automatic downloads of the malware without the user's knowledge.
Once executed, Clone may spread across local and networked drives, encrypting files as it goes. The ransomware also ensures its persistence by copying itself to the %LOCALAPPDATA% folder and adding entries to the system's Run keys, which ensures it reboots and runs automatically.
Removal Guide: How to Remove Clone Ransomware
If you find that your system has been infected with Clone ransomware, the best course of action is to use a professional anti-malware tool like SpyHunter to detect and remove the threat.
Download SpyHunter Now & Scan Your Computer For Free!
Remove this and any other malicious threats to your system by scanning your computer with SpyHunter now! It's FREE!
Step 1: Install SpyHunter
- Download SpyHunter and install it on your computer. If you cannot install it due to the ransomware, try restarting your computer in Safe Mode with Networking.
Step 2: Scan Your System
- Launch SpyHunter and run a full system scan. This will allow the software to detect all instances of Clone ransomware, along with any associated malware.
Step 3: Remove the Threat
- Once the scan is complete, SpyHunter will provide a list of detected threats, including Clone ransomware. Select Remove to eliminate the ransomware and any additional malware it may have installed.
Step 4: Restore Your Files (Optional)
- If you have a backup stored on an external device or cloud service, now is the time to restore your files. Unfortunately, since Clone uses strong encryption, you will not be able to recover your files without the decryption key unless you have a backup.
Step 5: Perform a Final Scan
- After removal, run another scan to ensure the system is clean and no remnants of the ransomware remain.
Preventing Future Infections: Best Practices
To avoid falling victim to Clone ransomware or other similar threats in the future, it’s essential to take the following preventive measures:
- Use Strong Passwords: Ensure your system’s credentials are robust, especially for RDP (Remote Desktop Protocol). Use a password manager to generate complex, unique passwords.
- Update Software Regularly: Keep your operating system, applications, and antivirus software up-to-date to protect against vulnerabilities that ransomware can exploit.
- Avoid Suspicious Links and Attachments: Do not open email attachments or click on links from unknown or suspicious sources.
- Implement Multi-Factor Authentication (MFA): Whenever possible, enable MFA for an extra layer of security on your accounts.
- Back Up Your Data: Store regular backups on external hard drives or cloud services. Ensure that backups are not connected to your main network to avoid them being encrypted in the event of an infection.
- Use a Reputable Antivirus Program: Invest in reliable antivirus software and perform regular scans to detect threats before they can cause significant damage.
Conclusion
Clone ransomware is a dangerous and sophisticated threat that encrypts files and demands a ransom for their release. As part of the Dharma ransomware family, it uses advanced tactics to ensure persistence and maximize the damage it causes. While removing Clone ransomware with SpyHunter is relatively straightforward, the encrypted files may be irretrievable without a backup or the decryption key.
By adhering to best practices for prevention and maintaining good security habits, users can significantly reduce the risk of falling victim to Clone ransomware or similar attacks in the future.
Download SpyHunter Now & Scan Your Computer For Free!
Remove this and any other malicious threats to your system by scanning your computer with SpyHunter now! It's FREE!